When you first deploy the Cisco AnyConnect VPN and try to connect right away, you’ll see this error.
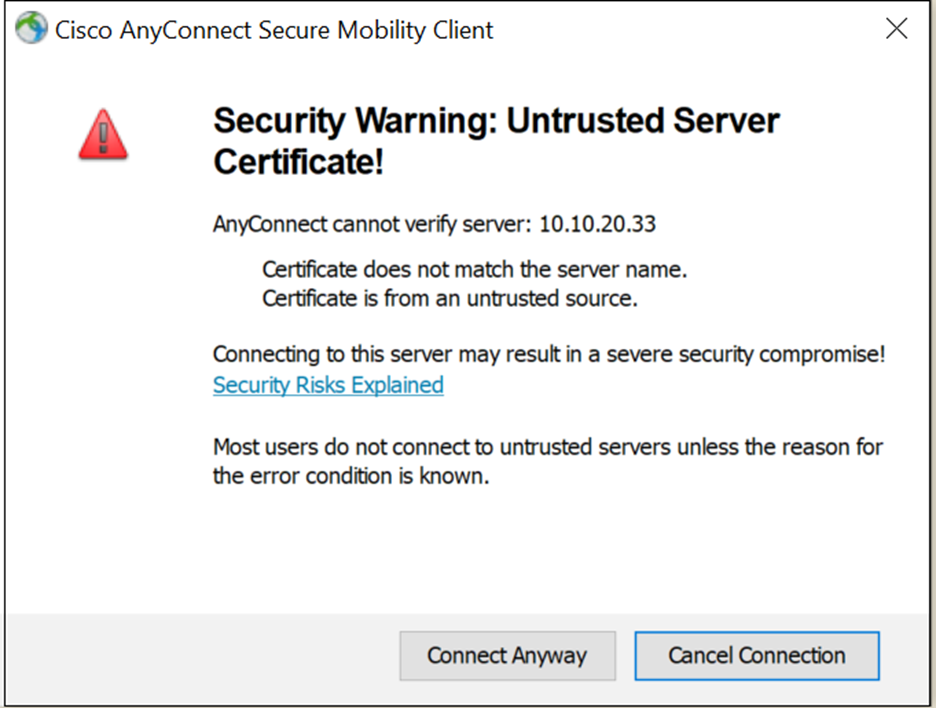
You can still connect but this tends to freak out most users (like any error). Here’s how we avoid flooding the helpdesk with unnecessary calls.
To fix the issue, we have two options:
- Import a certificate signed by the internal CA and install the internal CA certificate on all laptops (note, this isn’t commonly used and is actually a giant pain), OR
- Get an SSL certificate signed by a public CA (DigiCert, Verisign, Godaddy, etc).
The process is explained here for the ASDM. You can do this CLI but it’s a bit of a pain, so we tend to go with ASDM.
Here we show you how to generate the CSR, get the CSR signed by CA, and import the signed certificate back into the ASA alongside the Root CA certificate.
- Navigate to Configuration > Remote Access VPN > Certificate Management, and choose Identity Certificates.
- Click Add.
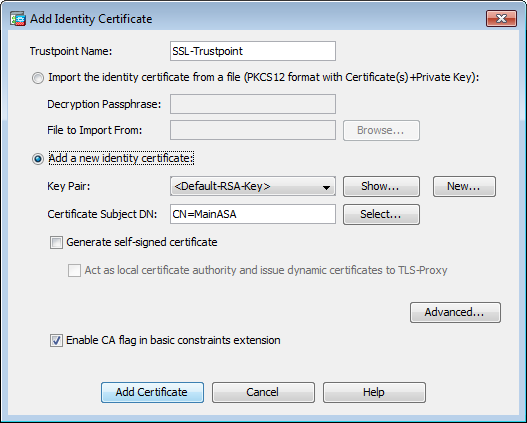
- You can name the Trustpoint whatever you want. We like to do something that signifies the service and year installed (e.g. VPN_2023).
- Click the Add a new identity certificate radio button.
- For the Key Pair, click New.
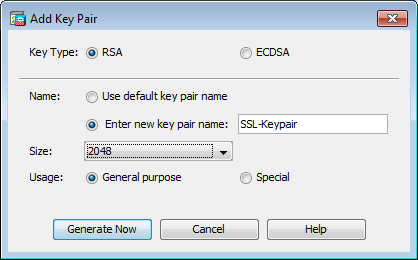
- Choose the Key Type – RSA or ECDSA. Usually RSA is fine int eh US
- Click the Enter new key pair name radio button. Identify the key pair name for recognition purposes.
- Choose the Key Size. Choose General Purpose for Usage if using RSA.
- Click Generate Now. The key pair are created.
- To define the Certificate Subject DN, click Select, and configure the attributes listed in this table:

- To configure these values, choose a value from the Attribute drop-down list, enter the value, and click Add.
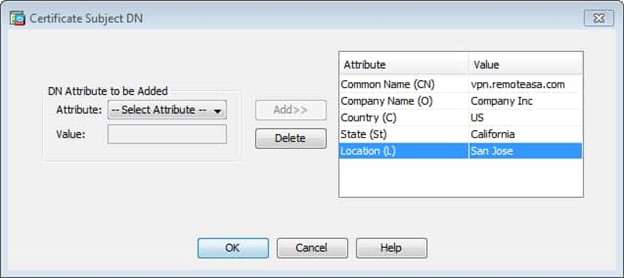
Note: Some third-party vendors require particular attributes to be included before an identity certificate is issued. If unsure of the required attributes, check with the vendor for details.
- After the appropriate values are added, clickOK. The Add Identity Certificate dialog box appears with the CertificateSubject DN field populated.
- Click Advanced.
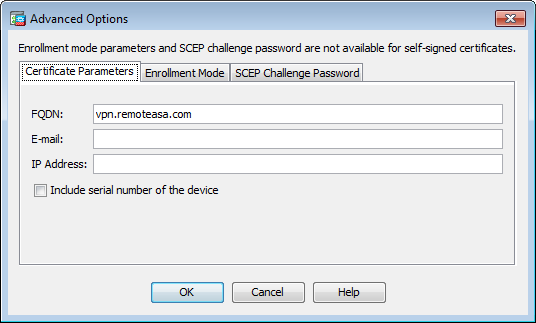
- In the FQDN field, enter the FQDN that is used to access the device from the Internet. Click OK.
- Leave the Enable CA flag in basic constraints extension option checked. Now, certificates without the CA flag can’t be installed on the ASA as CA certificates by default. The basic constraints extension identifies whether the subject of the certificate is a CA and the maximum depth of valid certification paths that include this certificate. Un-check the option to bypass this requirement.
- Click OK, and then click Add Certificate. A prompt displays in order to save the CSR to a file on the local machine.
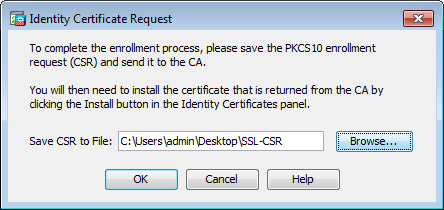
- Click Browse, choose a location in which to save the CSR, and save the file with the .txt extension.
Note: When the file is saved with a .txt extension, the PKCS#10 request can be opened and viewed with a text editor (such as Notepad++).
Next up, just follow your CA’s instructions for requesting a certificate using the CSR. Then we just have to install it. Also, if you’re not using GoDaddy, you will have to install the root and intermediate CA’s as well.
SSL Certificate Installation on the ASA
The installation steps given assume that the CA provides a PEM encoded (.pem, .cer, .crt) identity certificate and CA certificate bundle. Importing a .pfx will require a full import.
- Navigate to Configuration > Remote Access VPN > Certificate Management, and choose CA Certificates.
- The PEM encoded certificate in a text editor and copy and paste the base64 CA certificate provided by the third-party vendor into the text field.
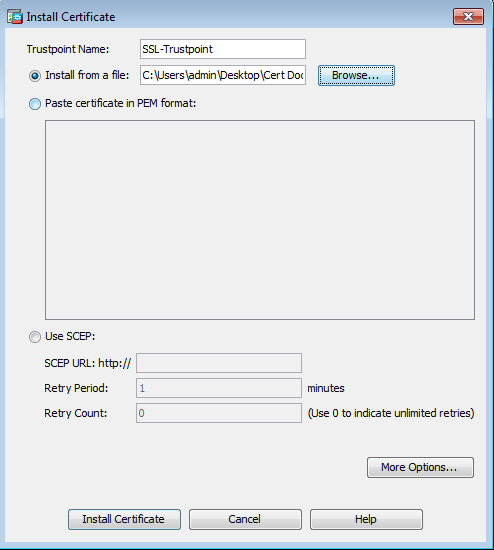
- Click Install certificate.
- Navigate to Configuration > Remote Access VPN > Certificate Management, and choose Identity Certificates.
- Select the Identity Certificate created previously. Click Install.
- Either click the option Install from a file radio button and choose the PEM encoded Identity certificate, or, open the PEM encoded certificate in a text editor and copy and paste the base64 Identity certificate provided by the third-party vendor into the text field.
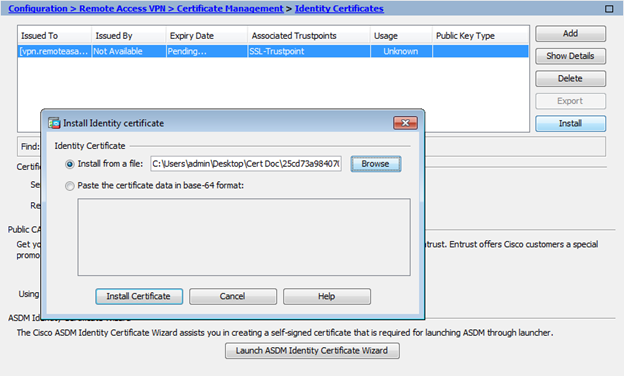
- Click Add Certificate.
- Navigate to Configuration > Remote Access VPN > Advanced > SSL Settings.
- Under Certificates, select the interface that is used to terminate WebVPN sessions. In this example, the outside interface is used.
- Click Edit.
- In the Certificate drop-down list, choose the newly installed certificate.
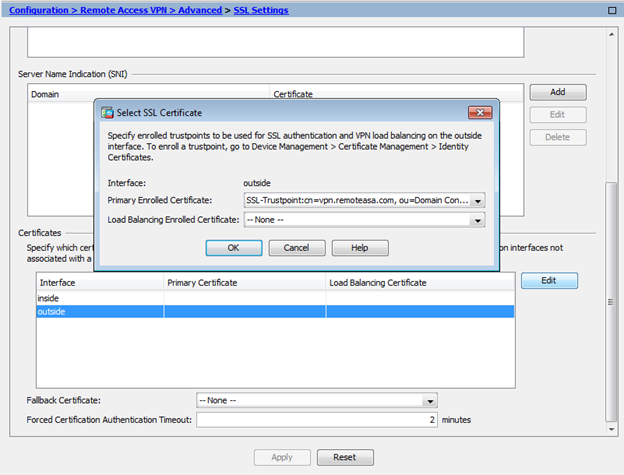
- Click OK.
- Click Apply. The new certificate is now utilized for all WebVPN sessions that terminate on the interface specified.
Want to learn more? Check out our Network Consulting solutions page for the other ways we can help.

