One of the best things a business can do is have redundant ISP (Internet Service Providers) connections. This ensures optimal uptime for their business. Even with the introduction of the Cisco FirePower Threat Defense firewall, The Cisco ASA and FTD with ASA firmware are still very popular IP firewalls.
This post describes how to configure a Cisco ASA firewall for redundant/dual ISP connections, using the IP SLA and track features. IP SLA will be configured in conjunction with the track feature to monitor the connection/reachability to the Primary ISP connection. In the event of failure, the primary default route will be removed and will failover to a backup route.
Configuration.
Configure the two outside interfaces, in this case PRIMARY and SECONDARY will be used to identify the outside interfaces.
interface GigabitEthernet0/0
nameif PRIMARY
security-level 0
ip address 1.1.1.1 255.255.255.0
interface GigabitEthernet0/1
nameif SECONDARY
security-level 0
ip address 2.2.2.1 255.255.255.0
Create NAT rules for traffic routed out of the primary and secondary interfaces. We need to do this for global NAT and static NAT rules. We like to create new objects for internal and external addresses. Don’t forget NAT rules for site to site VPN’s and Remote access VPN’s.
Global NAT
|
nat (INSIDE,PRIMARY) after-auto source dynamic any interface nat (INSIDE,SECONDARY) after-auto source dynamic any interface |
Static NAT
|
object network server_inside_pimary nat (INSIDE,PRIMARY) static server_outside_primary object network server_inside_secondary nat (INSIDE,SECONDARY) static server_outside_secondary |
VPN NAT
|
Nat (INSIDE,PRIMARY) static VPNSUBNET VPNSUBNET Nat (INSIDE,SECONDARY) |
Next, we’re going to create the SLA. This monitors the primary internet connections by sending pings out to a specific target.
|
sla monitor 1 |
Now we schedule the SLA process to start immediately with a lifetime of forever.
|
sla monitor schedule 1 life forever start-time now |
Then, create a track ID. The “rtr” references the SLA ID. The track ID will be used in conjunction with static default route.
|
track 100 rtr 1 reachability |
Next, define a default route via the PRIMARY interface, referencing the track object.
| route PRIMARY 0.0.0.0 0.0.0.0 1.1.1.254 1 track 100 |
Lastly, create a backup default route via the SECONDARY interface with an administrative distance greater than the tracked default route.
| route SECONDARY 0.0.0.0 0.0.0.0 2.2.2.254 100 |
Verification.
From a test computer ping an IP address on the internet, e.g. 8.8.8.8. Confirm traffic is being routed out of the PRIMARY interface.
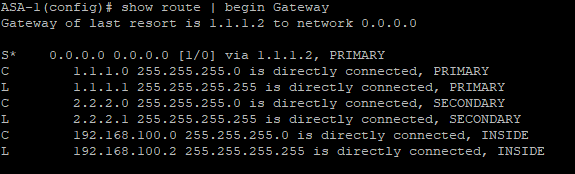
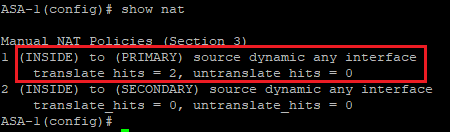
Confirm that traffic is hitting the correct NAT rule.
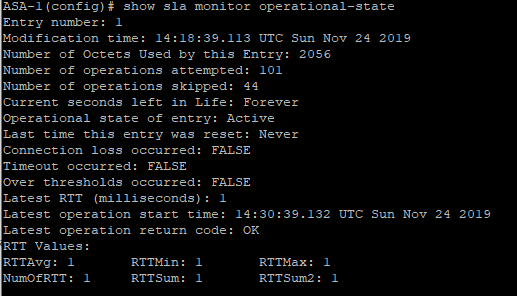
Confirm the status of the IP SLA enter the command show sla monitor operational-state, ensure timeout equals FALSE.
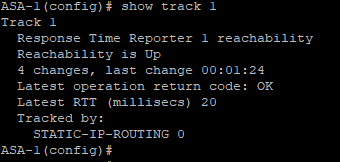
Confirm that reachabilty of the track is Up, use the command show track
Shutdown the interface of the PRIMARY interface and confirm the status of the reachability of the track is Down.
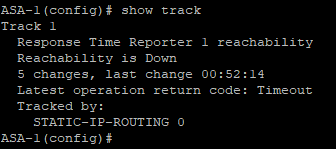
Confirm the default route is now via the SECONDARY interface.
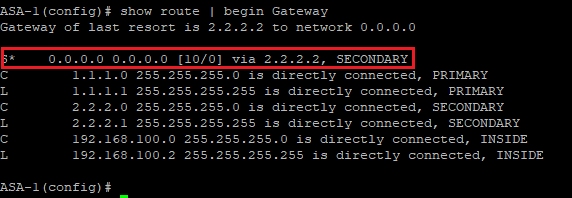
Confirm traffic is natted by the correct NAT rule.
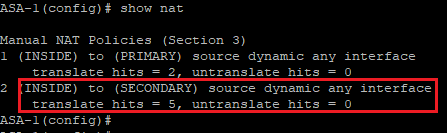
Re-establishing connectivity via the PRIMARY interface will result in the default route via the PRIMARY interface being installed in the routing table.
Want to learn more about other ways to help your network thrive? Check out our network consulting services and get in touch if you see something you like.

