The ASA allows applications to be dynamically excluded from an AnyConnect Remote Access VPN tunnel by specifying a list of domain names. This is useful when an organization does not wish to tunnel real-time voice/video applications such as Webex, Microsoft Teams/Office 365 etc. back to the VPN headend device.
With Dynamic Split tunneling, when the client communicates with the DNS domain name listed in the dynamic split tunnel list, AnyConnect will dynamically identify the IP address associated with the domain and exclude the traffic from the VPN tunnel. All other traffic not specified is tunneled to the ASA as normal.
This post does not cover configuring all the remote access VPN settings, only the configuration relating to setting up Dynamic Split tunneling.
ASA Configuration
The following configuration was tested on ASA version 9.12(3)9.
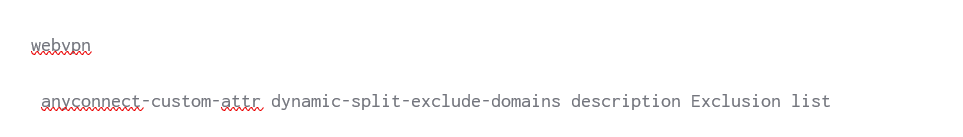
1. Define the AnyConnect custom attribute called dynamic-split-exclude-domains globally under WebVPN context.
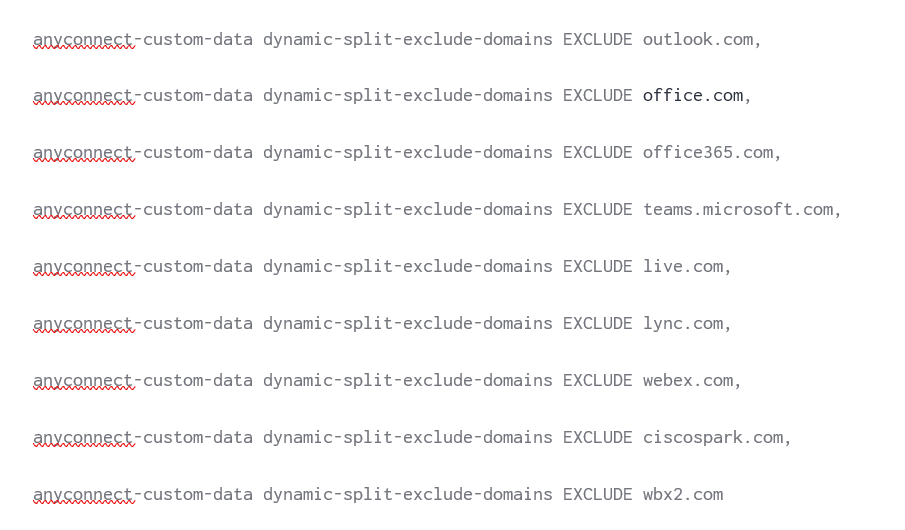
2. Create a list, in this instance called EXCLUDE, define each DNS domain name with a comma after the DNS domain name. IT IS IMPORTANT TO REMEMBER THE COMMA.
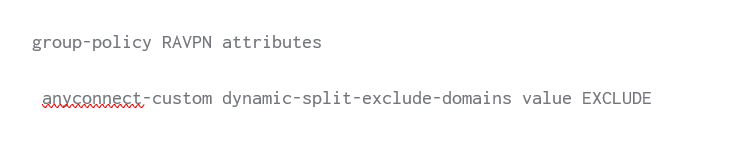
3. Modify the group-policy assigned to the tunnel-group (connection profile), reference the dynamic split tunnel exclusion list EXCLUDE.
Verification
Before we get started on verification, complete these three steps.
- Login to a laptop and authenticate to the VPN
- Open the AnyConnect Advanced Window
- Click the Statistics tab
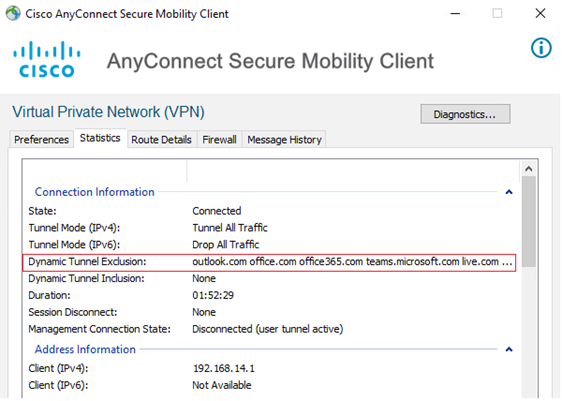
When Dynamic Split Tunneling is configured, the AnyConnect client should list the Dynamic Tunnel Exclusions.
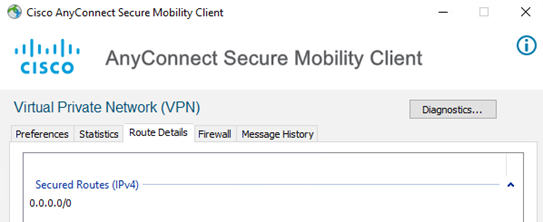
Next, click the Route Details tab. Notice there is only the Secured Routes of 0.0.0.0/0
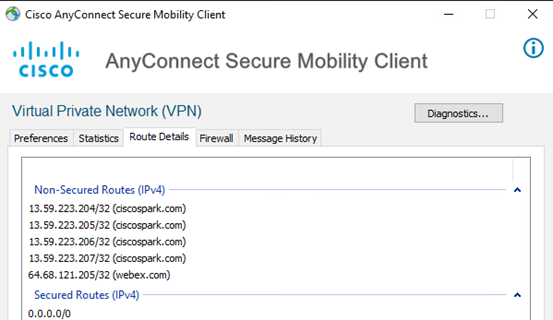
Send some traffic to any of the DNS domain names specified in the Dynamic Exclusion list., such as Webex.com, ciscospark.com etc.
Whenever the client computer communicates with a DNS domain name as defined in the Dynamic Exclusion list, AnyConnect will automatically add the IP address as a non-secured route, the traffic will not be tunneled back to the ASA.
Modifying the exclusion list
There does not currently appear to be a way to edit (add/remove) DNS domain names to the exclusion list.
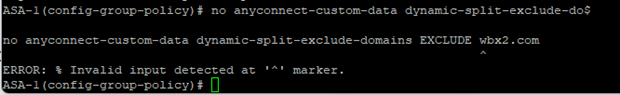
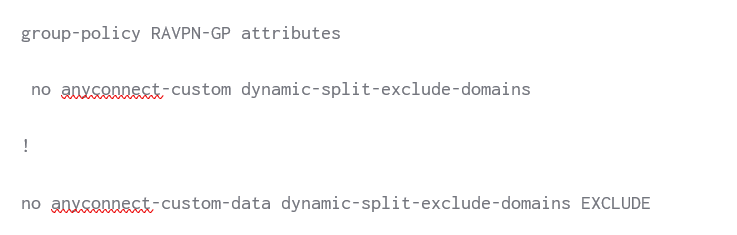
The only known method is removing the configuration under the group-policy and deleting the exclusion list before re-adding the commands as defined above.
If you want to learn more, you can check out some of our other IT network consulting services via the button below.

