We have a lot of clients that leverage AnyConnect as a VPN client asking us to enable MFA on their VPN. Most of them are already leveraging MFA utilizing Azure AD, so it makes sense to move their authentication to AAD from on-premise.
There are advantages to moving to RADIUS from on-premise to Azure AD, using SAML:
- Control in Azure AD who has access to Cisco AnyConnect with a bit more granularity.
- Enable your users to be automatically signed-in to Cisco AnyConnect with their Azure AD accounts.
- Manage your accounts centrally in the Azure portal.
- Simplified viewing and tracking of user logins without collecting logs form an Active Directory server.
To get started, you need the following items:
1. An Azure AD subscription. If you don’t have one, you can get a free account here.
2. Cisco AnyConnect single sign-on (SSO) enabled subscription. The app is free form the gallery.
3. Cisco ASA firmware 9.7(1) or higher – hopefully you’re above that!
Note, to support a load balanced VPN configuration, your ASA must be at ASA 9.16 at least.
Once you’re ready to go, the first step is to add The Cisco AnyConnect app to Azure AD form the Application Gallery.
-
- Sign in to the Azure portal using either a work or school account, or a personal Microsoft account.
- On the left navigation pane, select the Azure Active Directory service.
- Navigate to Enterprise Applications and then select All Applications.
- To add new application, select New application.
- In the Add from the gallery section, type Cisco AnyConnect in the search box.
- Select Cisco AnyConnect from results panel and then add the app. Wait a few seconds while the app is added to your tenant.
Now we have to configure and enable the AnyConnect Integration.
-
- In the Azure portal, on the Cisco AnyConnect application integration page, find the Manage section and select single sign-on.
- On the Select a single sign-on method page, select SAML.
- On the Set up single sign-on with SAML page, click the edit/pen icon for Basic SAML Configuration to edit the settings.
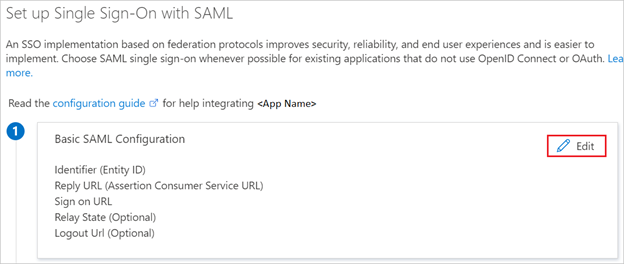
4. On the Set up single sign-on with SAML page, enter the values for the following fields:
In the Identifier text box, type a URL using the following pattern:
In the Reply URL text box, type a URL using the following pattern:
Note: <Tunnel_Group_Name> is case-sensitive and the value must not contain dots “.” and slashes “/”.
You will also need to create an app for each tunnel-group you have if you are using multiple profiles.
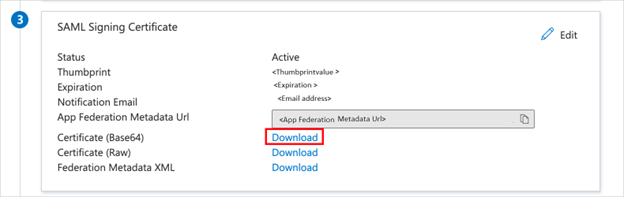
5. On the Set up single sign-on with SAML page, in the SAML Signing Certificate section, find Certificate (Base64) and select Download to download the certificate file and save it on your computer
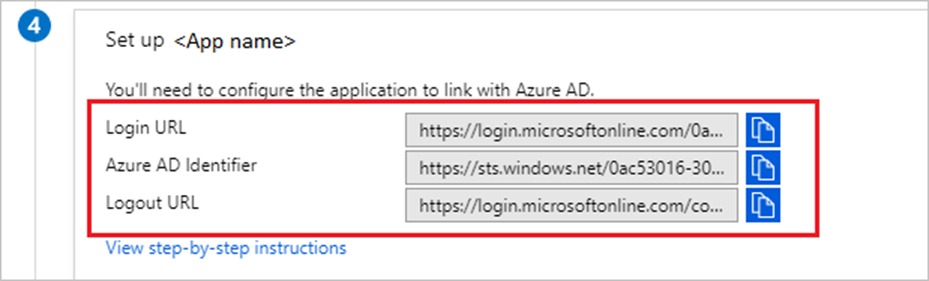
6. On the Set up Cisco AnyConnect section, copy the appropriate URL(s) based on your requirement.
Now we need to add either a test user or the group we want to enable for the VPN to the Cisco AnyConnect application.
-
- In the Azure portal, select Enterprise Applications, then select All applications.
- In the applications list, select Cisco AnyConnect.
- In the app’s overview page, find the Managesection and select Users and groups.
- Select Add user, then select Users and groups in the Add Assignment
- In the Users and groups dialog, select your test user or VPN group from the Users list, then click the Select button at the bottom of the screen.
- If you are expecting a role to be assigned to the users, you can select it from Select a Role. If no role has been set up for this app, you see “Default Access” role selected. Normally there is no additional role to assign.
- In the Add Assignment dialog, click the Assign
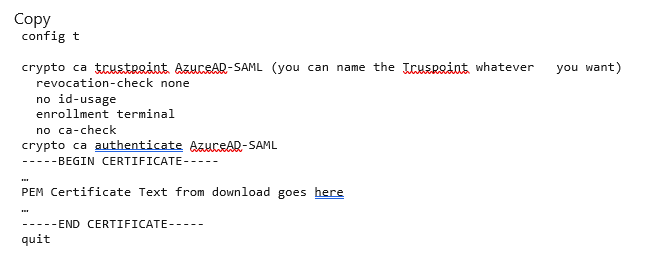
Now we’re configuring the ASA for SAML auth. CLI is the fastest but it can be done with the aSDM, that will be another article later.
1. First you will create a Trustpoint and import our SAML cert.
2. The following commands will provision your SAML IdP.
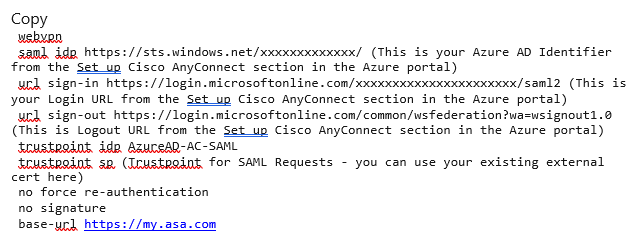
3. Now you can apply SAML Authentication to a VPN Tunnel Configuration.
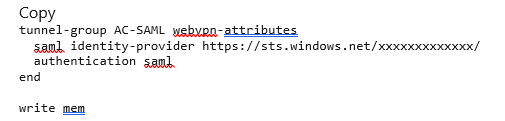
4. Then apply it to your tunnel group and you’re set. When you log in to that tunnel group, you’ll be re-directed to an Azure sign in.
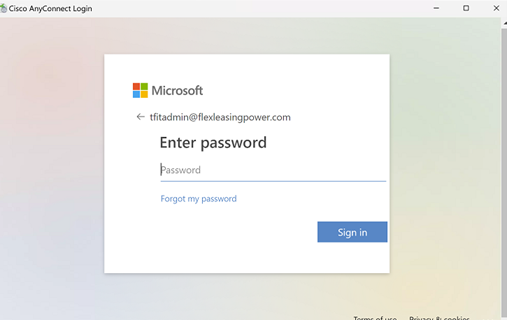
If you need to make changes to the IdP configuration, like update the idP certificate, you need to remove the SAML identity-provider configuration from your Tunnel Group and re-apply it for the changes to become effective.
If you want to learn more, you can check out some of our other IT network consulting services via the button below.

